智慧校园
智慧校园
川财要闻
【新闻网】
为美而生·为你而来
阳春三月,暖风拂面,又是一年春好时,第114个“国际妇女节”如期而到。3月8日下午,学院工会在美丽的龙...【详情】11
2024-03
学院召开2024年度科研工作会议
为落实学院“十四五”规划相关科研任务,围绕学院2024“质量年”安排部署,推动学院科研工作高质量发展...【详情】08
2024-03
校团委圆满召开2024年春学生干...
为顺利开展新学期学生工作,对2024年春季学期工作进行整体部署,提高学生干部综合能力,3月5日,校团委...【详情】07
2024-03
符刚院长接待博特产业技术有限...
2024年3月6日,博特产业技术有限公司总裁刘温泉一行到我校洽商校企合作相关事宜,学院院长符刚陪同交流...【详情】07
2024-03综合时讯
【新闻网】
罗潇副院长带队赴成都航空职业...
2024年3月8日,学校党委委员、副院长罗潇带队赴成都航空职业技术学院调研交流,深入推动校校合作,加强...【详情】09
2024-03
学院纪委召开基层党组织纪检委...
3月7日下午,学院纪委在行政楼912会议室召开第一批次基层党组织纪检委员履职情况调研座谈会。会议由党委...【详情】08
2024-03
四川护理职业学院护理系党总支...
2024年3月7日上午,四川护理职业学院护理系党总支书记黄鸷、副书记田炼等一行9人到我校交流党建工作。校...【详情】08
2024-03
学院纪委召开2024年第一次全体...
3月5日下午,学院纪委召开2024年第一次全体会议。会议由党委副书记、纪委书记余俊任主持。会议传达了习...【详情】06
2024-03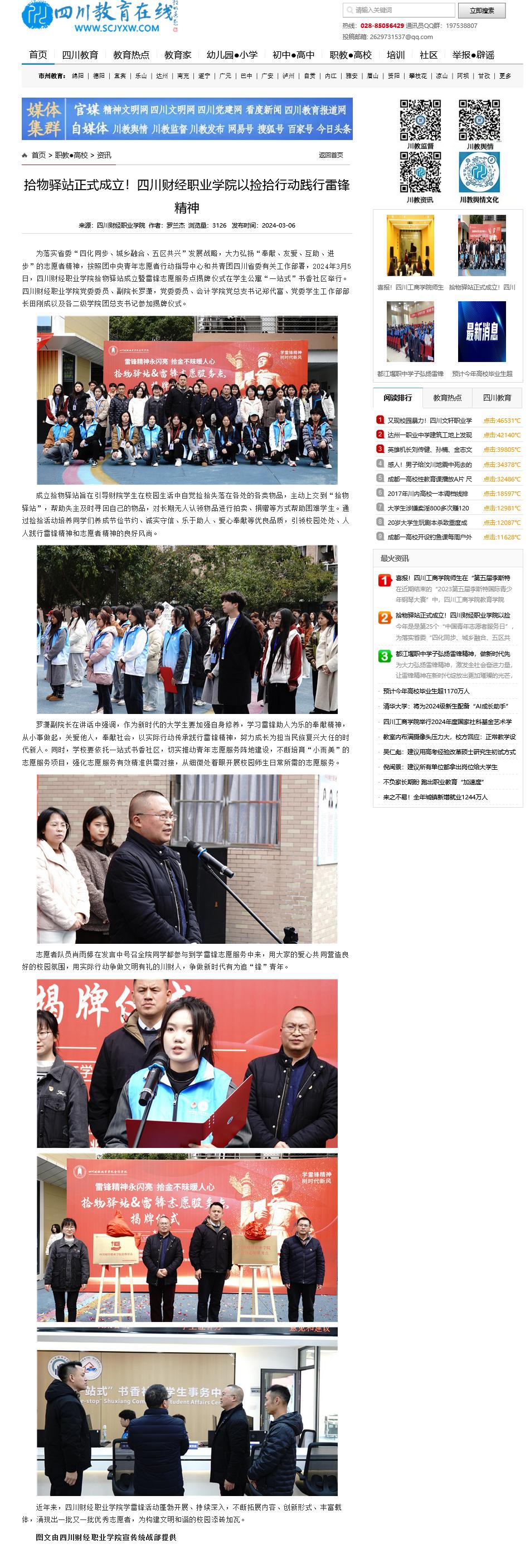
四川教育在线:拾物驿站正式成...
为落实省委“四化同步、城乡融合、五区共兴”发展战略,大力弘扬“奉献、友爱、互助、进步”的志愿者精神,按照团中央青年志愿者...【详情】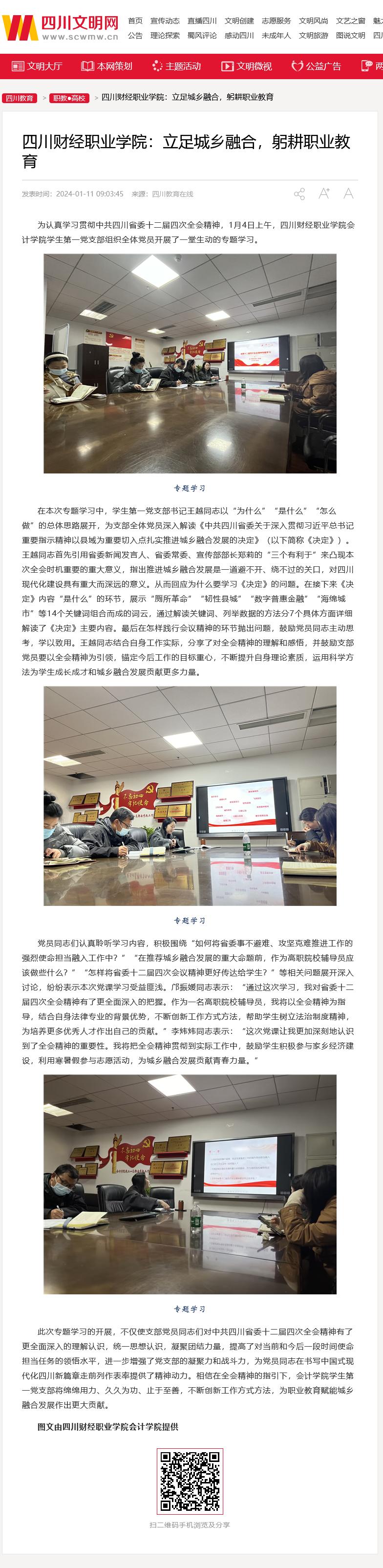
四川文明网:爱游戏官方网站...
为认真学习贯彻中共四川省委十二届四次全会精神,1月4日上午,爱游戏官方网站会计学院学生第一党支部组织全体党员开展了一堂生...【详情】
四川教育在线:四川财经职业学...
为认真学习贯彻中共四川省委十二届四次全会精神,1月4日上午,爱游戏官方网站会计学院学生第一党支部组织全体党员开展了一堂生...【详情】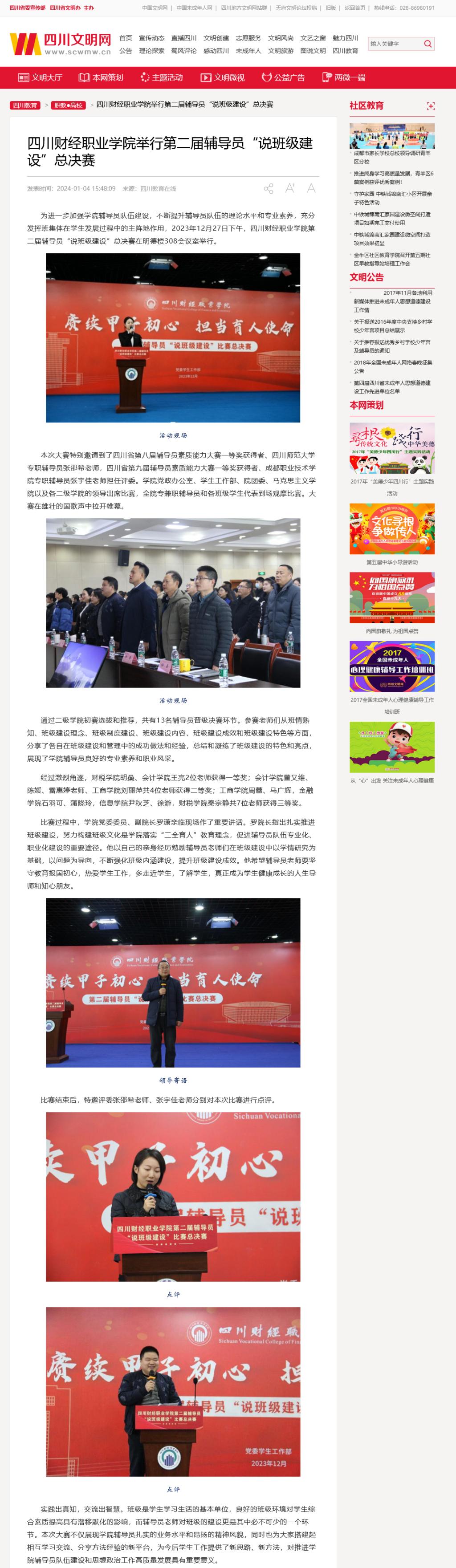
四川文明网:爱游戏官方网站...
为进一步加强学院辅导员队伍建设,不断提升辅导员队伍的理论水平和专业素养,充分发挥班集体在学生发展过程中的主阵地作用,2023...【详情】
学校地址:
成都市龙泉驿区驿都西路4111号 邮编:610101
联系电话:
028-84642011(含传真)/ 028-84642001(值班)
028-84642024(招生就业)